by Joel R. Voss aka. Javantea
jvoss@altsci.com
jvoss@myuw.net
Oct 28, 2005
This program connects to an identd server and asks for the information. This is an unintended consequence of the design of the server.
Identd is an interesting program. It searches /proc/net/tcp for a matching entry. The input is easy enough for a human to input into telnet if they have the localport and the remoteport. We get the localport from getsockname() and the remote port is the port that we are connected to. This will give us the user that is running the command.
jvoss@ASLinWs01:~$ telnet localhost 113 Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. ^] telnet> !netstat -panult | grep telnet (Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.) tcp 0 0 127.0.0.1:49492 127.0.0.1:113 ESTABLISHED 9793/telnet 49492,113 49492 , 113 : USERID : OTHER :1001 Connection closed by foreign host.
Sadly this does not work on mIRC by default. mIRC only opens the Identd server
during connection. A quick option flip gives us the proper result.
Received '43888, 113 : USERID : UNIX : Javantea\r\n'
It works mildly well with pidentd on Linux.
Received '51861 , 113 : USERID : OTHER :1001\r\n'
1001 is the first user created, which definitely is not enough information for
any good use.
Although identd is a vulnerability, it is not a very big one considering how well default implementations keep the data private. The trick is in fact a flaw in the protocol. It allows any internet user to get a user id or name just by connecting.
During the Botnet Tutorial, I stumbled upon
several open auth ports. I decided to check one. Here is the result and a
screenshot:
jvoss@ASLinLt07:~/recent/ident_scan$ python ident_scan.py 210.35.74.43 Received 220 Just Another FBI Honeypot ^^
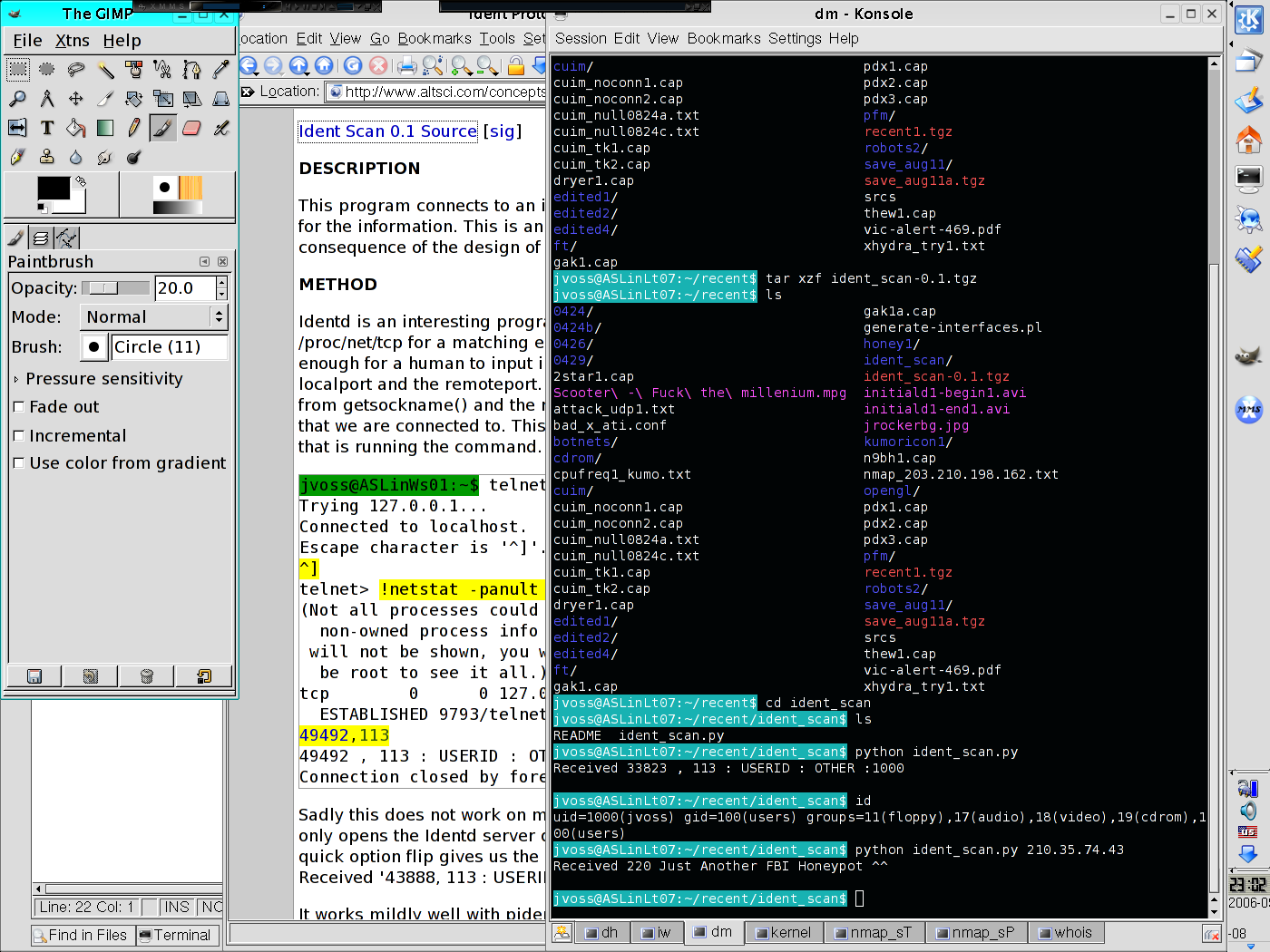
Not only did this freak us out, it was far too big a coincidence. We had been talking about the FBI and we had contact with the FBI (through Agora) that morning. But who would spit something out like that when you send data on port 113? No one else in the world uses ident_scan. A Google search for that phrase does not turn up any results (it's not a common tool?). The IP address is located in China. So that brought the botnet tutorial to an end.
python ident_scan.py [host [port]]The default command:
python ident_scan.py runs the scan on
127.0.0.1:113.
If you are interested in developing Ident Protocol Scan, feel free to e-mail me.