NetMap1 (aka UW Network Port Discovery Project)
Netmap1 (aka UW Network Port Discovery Project)
Who : You, Admins, and other people's computers
What : Open ports
Where : on the network protocols
When : quickly while no one is watching
How : use special options on nmap, parse it with python, export it to mysql
Why : Because knowledge will help you attack, defend, and learn in general
What does Nmap do?
Nmap is a port scanner that has a lot of really cool functionalities. The drawback of having a
lot of cool functionalities is picking the right one to use. That is why Netmap1 chooses them
for you. Specifically, Netmap1 does two things:
1) Ping all hosts in the range.
nmap -sP -oX ping1.xml --host_timeout 1000 192.168.0.*
2) Scan for specific ports.
nmap -sS -P0 -T2 \
-p "21,22,23,25,37,53,80,113,135,139,443,445,\
1025,1433,3306,3389,5800,5900,6000,6881-6889" \
-oX port1_192.168.0.1.xml 192.168.0.1
When we are done with that, we can parse the information and store it in a database where we
can view it later.
Why do admins look for packets?
Being oblivious to network information is likely to ensure the brief existence of the network. Admins have a job to ensure that bandwidth is used correctly. Viruses ravage well-connected networks. Even if your network is very healthy, every administrator's curiosity ought to tell them that it's useful to get information about their network.
On the other hand, blatant packet capturing is a serious violation of privacy. If an administrator wants to avoid massive lawsuits, they will keep their nose out of people's business. What they must do instead is to target and log certain activities.
What would an admin look for?
If we are given the ability to log only things that are important to network health, what do we log? I would put a counter on the router to count packets that outputs to a graph. Knowing network statistics over time will give us a good overview of what is happening. If you split the packets into packet types, we can get statistical analysis of what type of things are happening. If we split that into ports, we can understand what types of things are going on. Admins these days go a step further and also make a graph of interior hosts usage.
After statistical analysis they need an IDS that will trigger alarms on certain signature activity. They must be fairly specific, because if they are too general, they will have no end to alarms. They can put alarms on certain hosts (a honeypot). This would be bad news for Netmap1 because we're doing a full scan of the ip range. Why would a network administrator discourage the mapping of their network? People who scan networks are either administrators or hackers. Since administrators don't expect anyone in their userbase to be administrators, they assume that anyone doing network mapping is a hacker. Administrators that place security high on their priority list, have large user bases, and are familiar with network mapping are not as paranoid about having network mappers on their network. They might see it as an opportunity to re-evaluate their latest scan of the network.
What would an admin see if he looked?
Good question. Here we are. If an admin was dumping all connections to their honeypot,
and you are doing a -PT scan (TCP scan) they would see something like this:
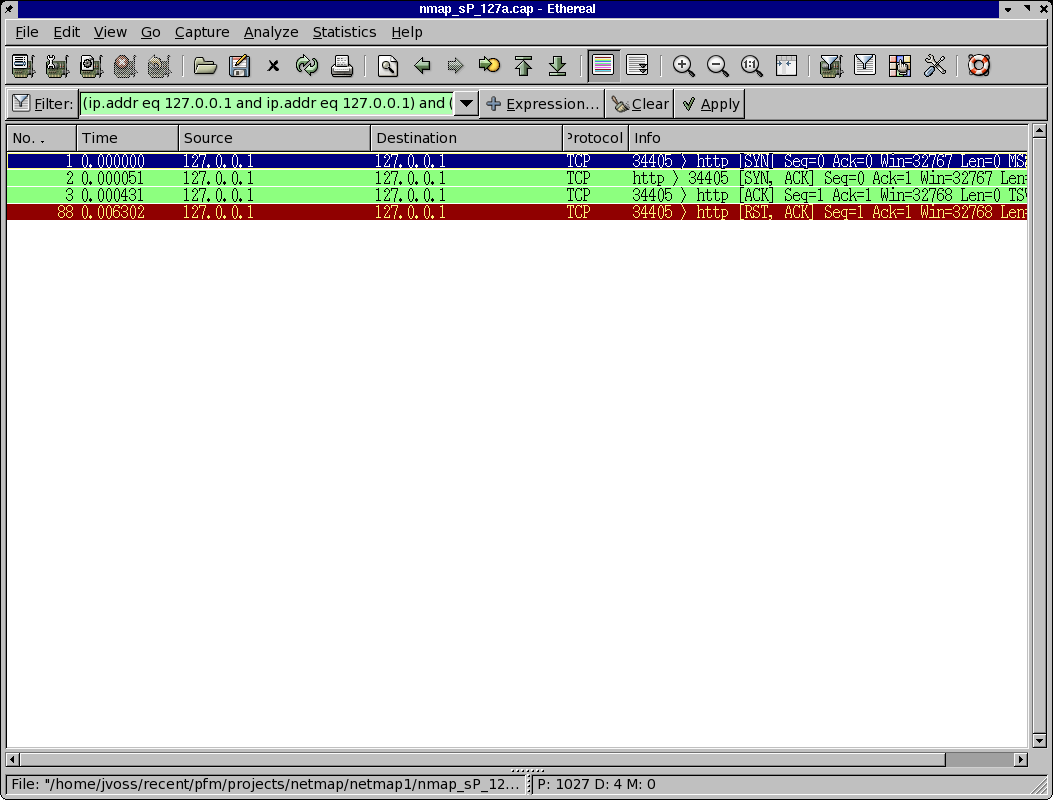
If they were dumping all connections to port 80 on their network in promiscuous mode,
and you are doing a -PT scan (TCP scan) they would see something like this:
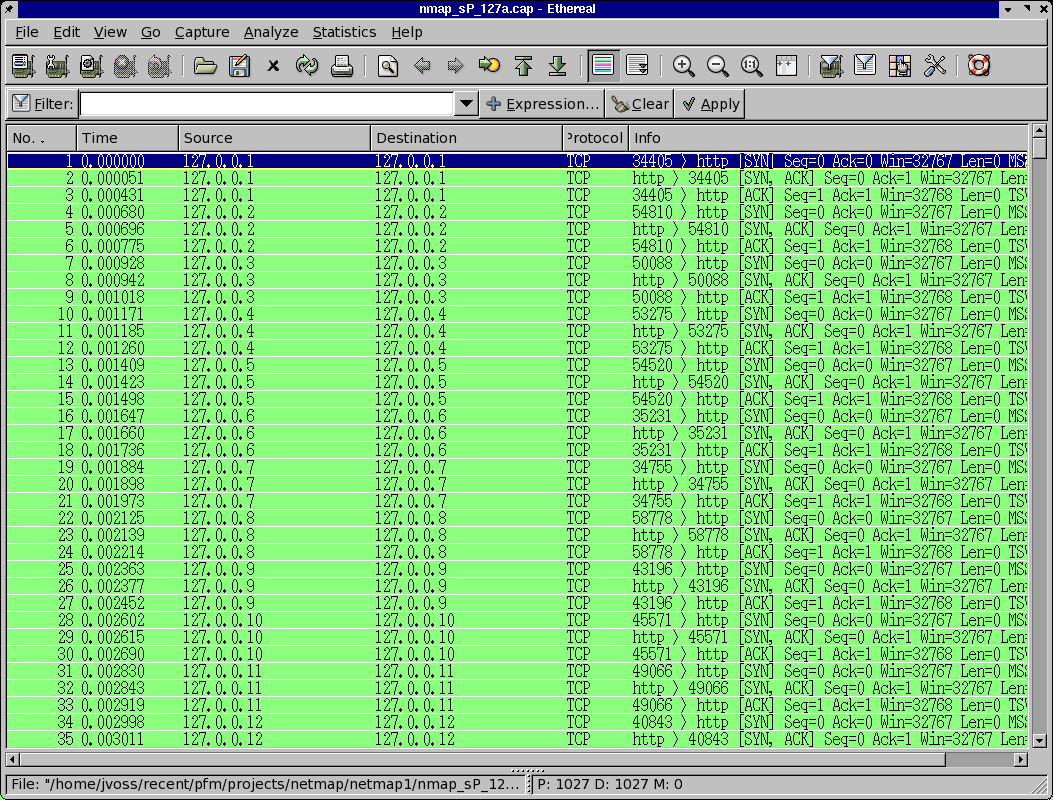
If they were dumping all connects to port 80 and ICMP on their network in promiscuous mode,
and you are doing a -PB scan (TCP+ICMP scan) they would see something like this:
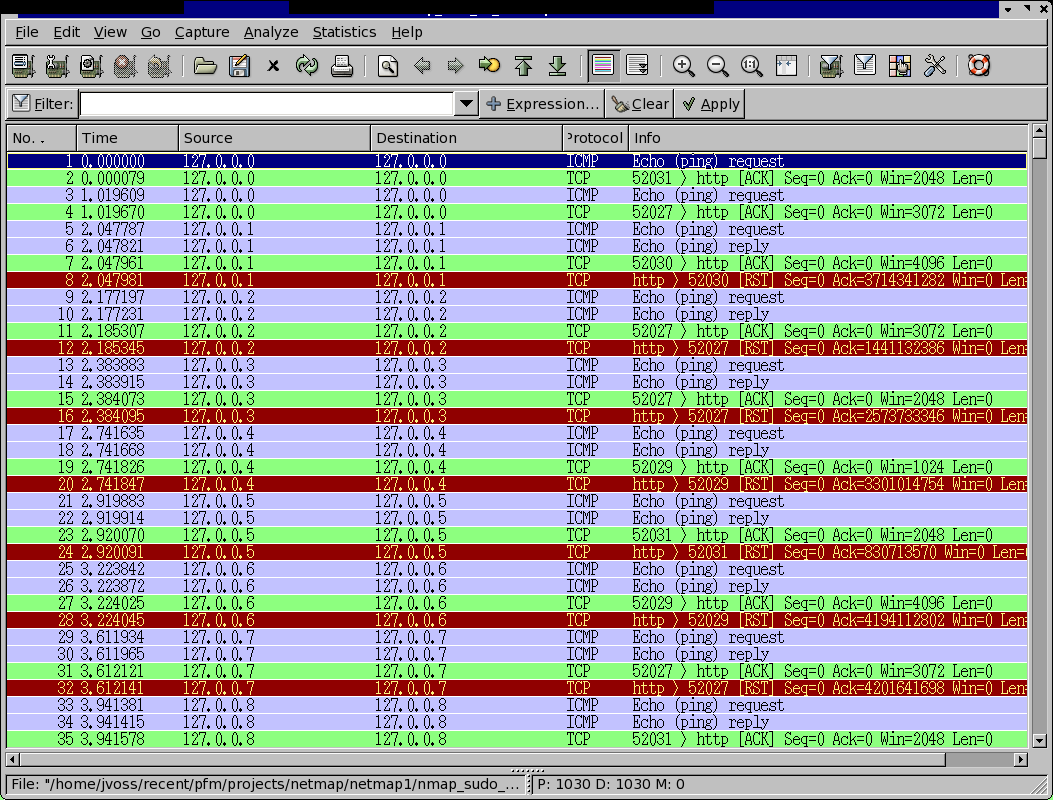
If they were dumping all connections to their honeypot,
and you are doing a -sS scan (SYN scan) they would see something like this:
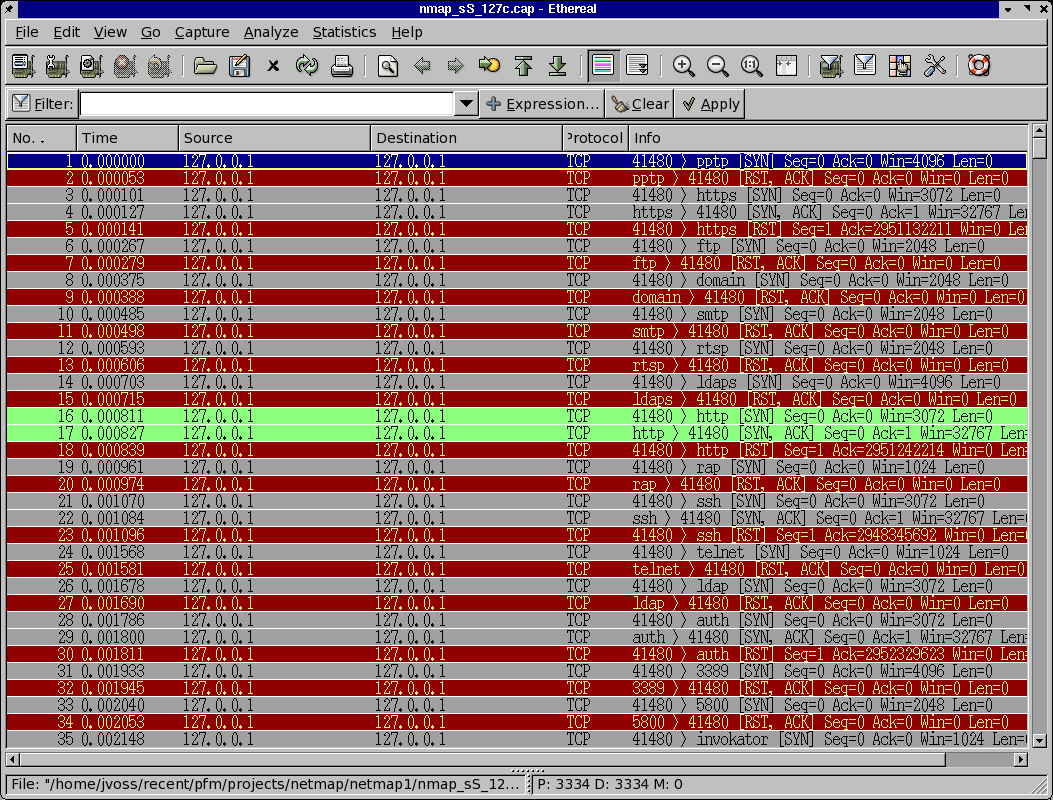
A full dump violates general ethical code, but unfiltered, it won't notice nmap with all the
traffic that normally goes through. HTTP traffic sends 2 packets per second but is human
limited looks a bit like this:
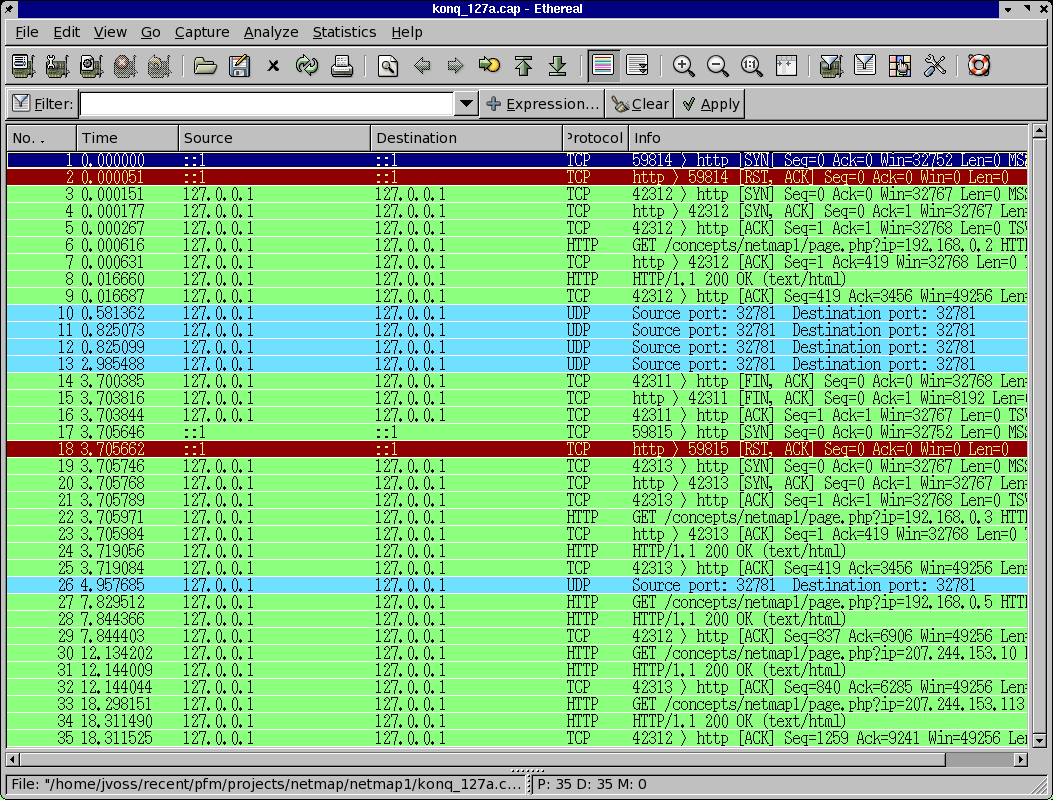 HTTP traffic accounts for 40% of all internet traffic.
HTTP traffic accounts for 40% of all internet traffic.
BitTorrent sends 74 large packets per second at 35 kBps looks like this:
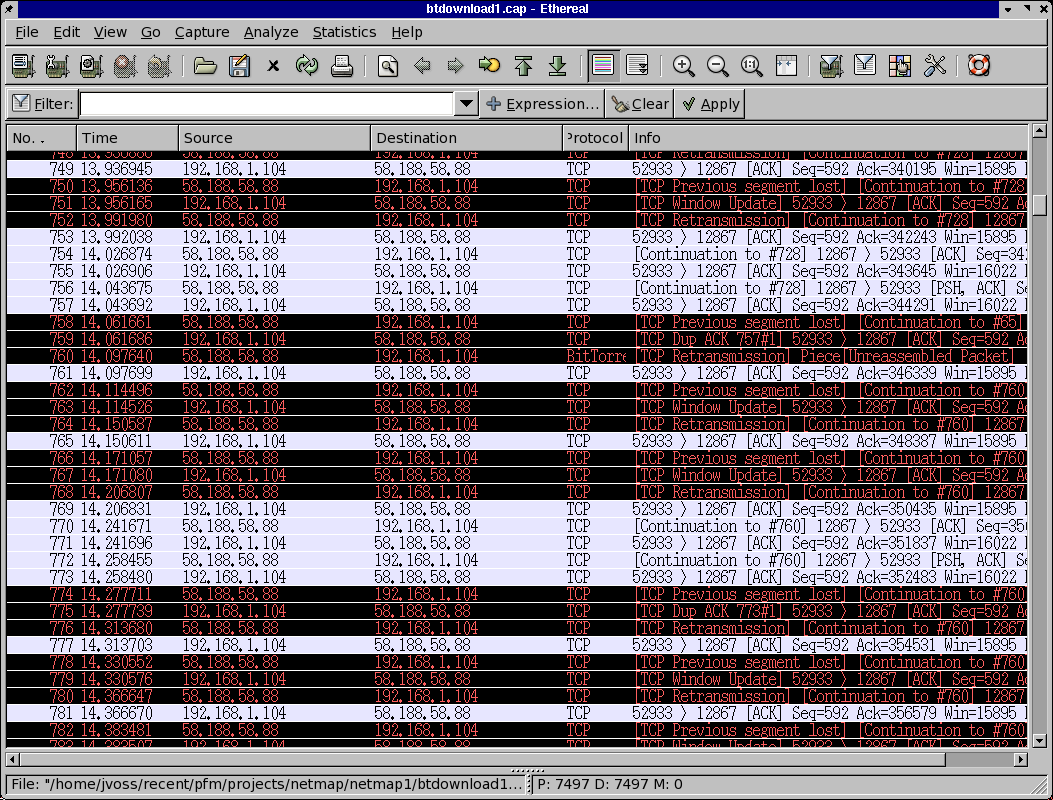 BitTorrent accounts for 30% of all internet traffic.
BitTorrent accounts for 30% of all internet traffic.
Source: http://www.cachelogic.com/research/2005_slide06.php
Nmap on default SYN scan mode (-T3) sends 12819 packets per second.
Netmap1 (-sS -T2) sends 5.7 packets per second.
Why do we want to slow down Nmap?
Nmap sends 1656 packets and receives the the same. It sends this in 21 seconds on fast connections (ethernet or loopback). On slow connections (DSL) it takes several minutes. Slowing it down is a polite thing to do and also a smart thing to do. 29 SYNs multiplied by 200 hosts over 11 * 200 seconds might go under the radar. 1656 * 200 over 22 * 200 seconds might get caught by a honeypot with an Nmap detector.
Getting caught should not be your only concern. DoSing some poor idiot running a 486 on RoadRunner Cable is not fun for anyone. Politeness on the shared networks is a must. Dan Kaminsky can do a 10Mbps attack on DNS because he's a researcher with a lot of backing. You, fellow researcher, are a guest in the domain of the admins who keep the network running. If you want to research, do so quietly.
Why isn't an admin interested in me?
A person who scans the network is not a threat. They are looking for boxes to exploit, yes. When you think of port scanning, what should immediately pop into your head is: Alice has port 445 open, let's try the LSASS exploit on her!
The savvy administrator keeps and eye on virus ridden boxes, people attacking network services, and people doing anomalous things. If the administrator is scanning the network for the same thing that the network scanner is, then they will not fear the 'sensitive' data that the 'hacker' will collect.
You will run into the non-savvy administrator quite often (often Windows administrators) that will not understand Network Mapping and will associate the word hacker with virus deployer, spammer, attacker, and intruder. They will say that an nmap scan is the same thing as an attack itself.
Running Nmap as fast as it will go on a high bandwidth connection targeting a low bandwidth server (DSL or Cable *owch*) is very similar to a simple DoS attack. However, if you use good practices and run it slowly (-T2), you will not harm anything. All port information is public knowledge no matter whether it's encrypted, super-secure, or Windows 98 with 5000 viruses running on it. This is a public network, you are sharing bandwidth, firewalls, vpns, etc are technical solutions to any port problem imaginable. Do not allow anyone to tell you to stop network mapping. On the flip side, try to be polite and don't nmap something more than their fair share.
From the Nmap man page!
GENERAL OPTIONS
None of these are required but some can be quite useful. Note that the -P options can
now be combined -- you can increase your odds of penetrating strict firewalls by send-
ing many probe types using different TCP ports/flags and ICMP codes.
-P0 Do not try and ping hosts at all before scanning them. This allows the scanning of
networks that don't allow ICMP echo requests (or responses) through their firewall.
microsoft.com is an example of such a network, and thus you should always use -P0 or
-PT80 when portscanning microsoft.com.
-PT [portlist]
Use TCP "ping" to determine what hosts are up. Instead of sending ICMP echo request
packets and waiting for a response, we spew out TCP ACK packets throughout the target
network (or to a single machine) and then wait for responses to trickle back. Hosts
that are up should respond with a RST. This option preserves the efficiency of only
scanning hosts that are up while still allowing you to scan networks/hosts that block
ping packets. For non root users, we use connect(). To set the destination ports of
the probe packets use -PT<port1>[,port2][...]. The default port is 80, since this port
is often not filtered out. Note that this option now accepts multiple, comma-separated
port numbers.
-PS [portlist]
This option uses SYN (connection request) packets instead of ACK packets for root
users. Hosts that are up should respond with a RST (or, rarely, a SYN|ACK). You can
set the destination ports in the same manner as -PT above.
-PU [portlist]
This option sends UDP probes to the specified hosts, expecting an ICMP port unreachable
packet (or possibly a UDP response if the port is open) if the host is up. Since many
UDP services won't reply to an empty packet, your best bet might be to send this to
expected-closed ports rather than open ones.
-PE This option uses a true ping (ICMP echo request) packet. It finds hosts that are up
and also looks for subnet-directed broadcast addresses on your network. These are IP
addresses which are externally reachable and translate to a broadcast of incomming IP
packets to a subnet of computers. These should be eliminated if found as they allow
for numerous denial of service attacks (Smurf is the most common).
-PP Uses an ICMP timestamp request (code 13) packet to find listening hosts.
-PM Same as -PE and -PP except uses a netmask request (ICMP code 17).
-PB This is the default ping type. It uses both the ACK ( -PT ) and ICMP echo request (
-PE ) sweeps in parallel. This way you can get firewalls that filter either one (but
not both). The TCP probe destination port can be set in the same manner as with -PT
above. Note that this flag is now deprecated as pingtype flags can now be used in com-
bination. So you should use both "PE" and "PT" to achieve this same effect.
SCAN TYPES
-sS
TCP SYN scan: This technique is often referred to as "half-open" scanning, because you don't open a full TCP connection. You send a SYN packet, as if you are going to open a real connection and you wait for a response. A SYN|ACK indicates the port is listening. A RST is indicative of a non-listener. If a SYN|ACK is received, a RST is immediately sent to tear down the connection (actually our OS kernel does this for us). The primary advantage to this scanning technique is that fewer sites will log it. Unfortunately you need root privileges to build these custom SYN packets. This is the default scan type for privileged users.
-sT
TCP connect() scan: This is the most basic form of TCP scanning. The connect() system call provided by your operating system is used to open a connection to every interesting port on the machine. If the port is listening, connect() will succeed, otherwise the port isn't reachable. One strong advantage to this technique is that you don't need any special privileges. Any user on most UNIX boxes is free to use this call.
This sort of scan is easily detectable as target host logs will show a bunch of connection and error messages for the services which accept() the connection just to have it immediately shutdown. This is the default scan type for unprivileged users.
Questions?
Download Netmap1 at: https://www.altsci.com/concepts/netmap1.htmlFind this talk online at: https://www.altsci.com/concepts/netmap1_talk.html
This talk was created as part of the slides1 project. While it lacks a homepage, it can be downloaded at: Slides1 Version 0.2.