Oct 10, 2010 10:43 am
No files officially released yet. See below.
Firmware hacking is an impressively difficult yet rewarding task. Most people are afraid of it because it depends on reversing binaries for embedded architectures that do not have good tools. Many tools that do exist are expensive and have a high learning curve even for experts in the field. Firmware hacking is actually a fun and simple process if you know what you're looking for. Projects for cell phones, video game consoles, and calculators are often out of the league of amateurs until the initial work is done. After the system has been successfully hacked, the code (if made available as open source) can be modified by anyone to improve the software.
Read more »
Aug 10, 2010
Sudo and Su Bruteforce 0.1 [sig]
Two years ago I noticed that su and sudo both contain a fatal flaw: administrator passwords. Administrator passwords have found themselves at the core of our security. OpenSSH does not allow root to login by default because on rare occasion administrator passwords can be bruteforced. Nearly all Linux and BSD systems recognize this. Some system administrators still don't recognize this due to business constraints. Users that have insecure passwords can be bruteforced if an attacker knows their name. The common system of first letter and last name or handle as the username gives an attacker a good list of users to bruteforce. How many administrators use the username jsmith? How many administrators use the username admin? Su and sudo may be considered harmful if we consider that usernames can be learned and that passwords can be bruteforced.
Removing the password component, we can compare sudo and su to the Windows Vista and Windows 7 administrator access security model: give a user administrator access when they ask for it. This person must be designated as an administrator by the original owner of the system. This seems obvious and tautological but we have yet to introduce an attacker with two different methods of attack.
Read more »
July 18, 2010
Xor is a binary operation that is versatile and not easily replaced. It represents a logical truth that is effective and seductive. Today I will give sixteen good reasons to love xor. If you are a computer scientist, programmer, or hacker and you don't use xor from time to time, you are doing something wrong.
Read more »
July 17, 2010
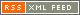
A long time ago I described a method of creating realistic anime hair with The GIMP. Today I reproduce that method with a small limit: 30 minutes or less. Most people want hair done in less than 30 minutes. Anime or manga artists want it done in seconds. But once you've done this style once, you'll have good reason to put in a few minutes. Shojo comics and ren-ai games use this realistic style on very rare occasion to portray texture, depth, emotion, or something else. The reason why I find myself using it instead of my normal style of outlining sharp tufts of hair is for dramatic effect, showing people not a green haired mahou tsukai (魔法使い) but a living breathing shaded person. Even if they are fictional I like my characters to have some sort of reality because it improves my ability to tell a story.
Minutes 1-3
Enough with the art, let's get down to the tech. The first thing to do is to draw the shape of the hair with large or medium size brush as seen below. This should only take you a moment because you should know what shape the hair will look. It's important that you draw this on a separate layer and never draw on it because you'll need it later. Trust me.