
HTTP Fuzzer: http_jrsfuzz1.py
SMTP Fuzzer: smtp_jrsfuzz1.py
DNS Fuzzer: dns_jrsfuzz1.py
HTTPS Fuzzer: https_jrsfuzz1.py
PDF Fuzzer: pdf_jrsfuzz1.py
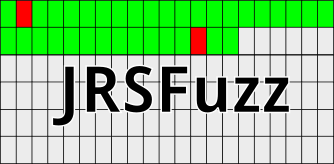
JRSFuzz is a ridiculously simple dumb fuzzer. It aims for coverage in TLV and single-byte token grammars. It obviously cannot attempt to fuzz word-based grammars without heavy modification. If you wish to add JRSFuzz to a smart fuzzer like Peach, it should take very little effort. Its method is bound to 256 * len(data) which means that it will finish very quickly with short data and will take linearally longer for longer data. Its method is to increment each byte separately from 0 to 255. For example, fuzzing the first line of the canonical HTTP request line would look like:
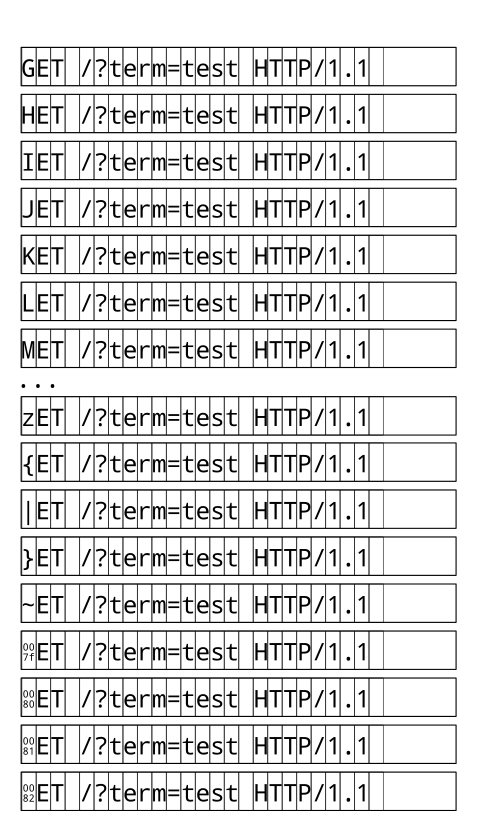
\x00ET / HTTP/1.1\r\n \x01ET / HTTP/1.1\r\n \x02ET / HTTP/1.1\r\n \x03ET / HTTP/1.1\r\n ... 0ET / HTTP/1.1\r\n 1ET / HTTP/1.1\r\n 2ET / HTTP/1.1\r\n 3ET / HTTP/1.1\r\n 4ET / HTTP/1.1\r\n ... \xfdET / HTTP/1.1\r\n \xfeET / HTTP/1.1\r\n \xffET / HTTP/1.1\r\n G\x00T / HTTP/1.1\r\n G\x01T / HTTP/1.1\r\n G\x02T / HTTP/1.1\r\n G\x03T / HTTP/1.1\r\n ...And so on. A graphic for the same:
To write a new file format fuzzer, use pdf_jrsfuzz1.py as a base.
If you want gdb to catch crashes or first chance exceptions, see gpg_jrsfuzz1.py as a base.
To write a new HTTP-alike fuzzer, use http_jrsfuzz1.py as a base.
To write a new TLS-wrapped fuzzer, use https_jrsfuzz1.py as a base.
To write a new SMTP-alike fuzzer, use smtp_jrsfuzz1.py as a base.
To write a completely new fuzzer, use the following code:
from __future__ import print_function import jrsfuzz import sys def main(): filename = 'fuzz_input.bin' if len(sys.argv) > 1: filename = sys.argv[1] #end if # Your file data = open(filename, 'rb').read() lines_output = len(data) * 256 print("%i outputs, %3.3f MB" % (lines_output, lines_output*len(data)/(1<<20)), file=sys.stderr) for i in range(lines_output): x = jrsfuzz.JRSFuzz(data, i) # Your consumer consumer(x) #next i #end def main() if __name__ == '__main__': main() #end if
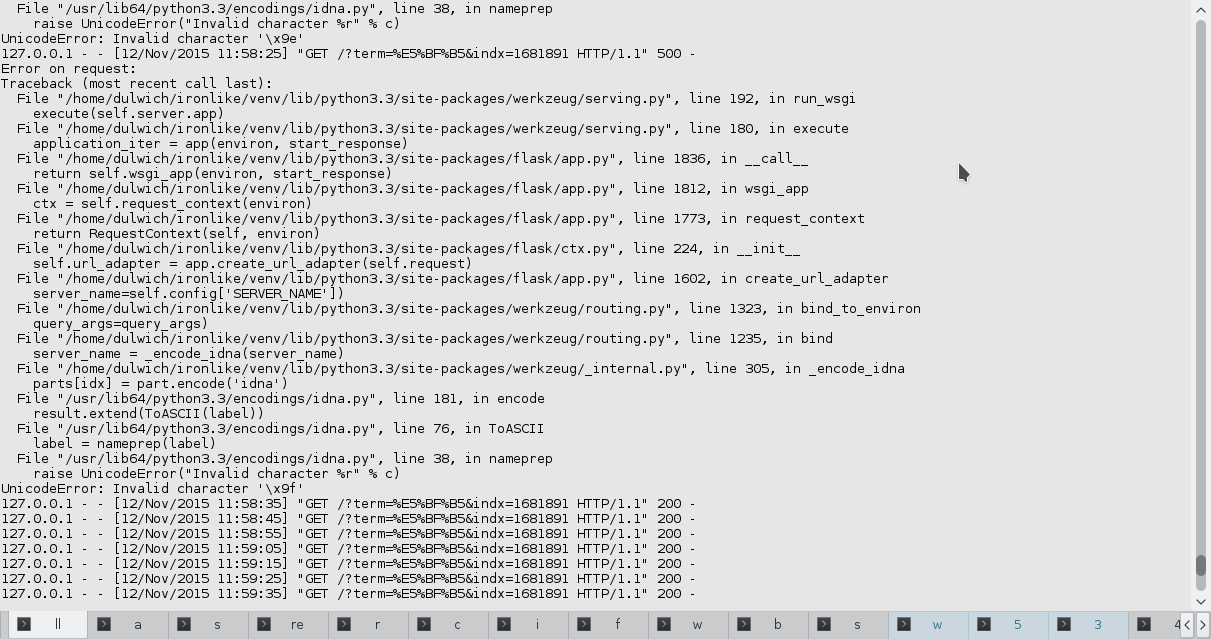
HTTP fuzzer found bugs in werkzeug:
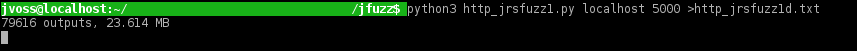
HTTP fuzzer running smoothly:
Heap buffer overflow read in openjpeg imagetopnm [reported]
valgrind -v opj_decompress -i fuzzfile0kqh22_c.jp2 -o fuzzfile0kqh22_c.jp2.ppmNull Dereference in tcd_malloc_decode_tile [reported]
openjpeg-1.5.2/build/bin/j2k_to_image -i ./jp2/fuzzfile8_76ff.jp2 -o ./jp2/fuzzfile8_76ff.jp2.test.ppm